In my previous article, i explained about the Ravan Tool. Now let us see how to use the Ravan for cracking passwords.
Step1:
If hash is successfully submitted, it would return a URL. Now you just need to send this URL to all your friends and ask them to click the start button.
That is it. Once your friends click start they would be doing pieces of the work and submitting results back.
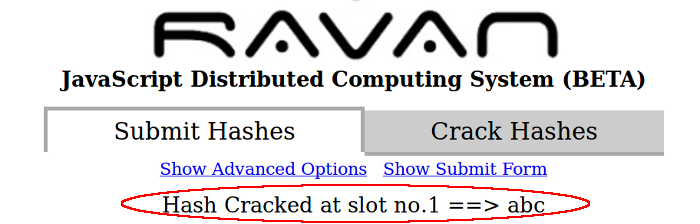
The main page would constantly monitor the progress of the cracking process and manage it across all the workers. You would be able to see the stats throughout the process, once the hash is cracked the clear-text value is displayed
Requriments:
Lot of Friends :
Ravan is Distributed password cracking method. So you will need lot of friends who have Pc with Internet connection. The speed of cracking will increase based on the number of pc contribute in the cracking.How to use Ravan?
- Go to http://www.andlabs.org/tools/ravan.html
- Enter the value of the hash that must be cracked
- Enter the value of the salt, if it is not a salted hash then leave it blank
- Enter the charset. Only these characters will be use in the brute force attack
- Select the hashing algorithm (MD5, SHA1, SHA256, SHA512)
- Select the position of the salt. (clear-text+salt or salt+clear-text)
- Hit ‘Submit Hash’
If hash is successfully submitted, it would return a URL. Now you just need to send this URL to all your friends and ask them to click the start button.
The main page manages the cracking so it must not be closed or the cracking would fail.
That is it. Once your friends click start they would be doing pieces of the work and submitting results back.
The main page would constantly monitor the progress of the cracking process and manage it across all the workers. You would be able to see the stats throughout the process, once the hash is cracked the clear-text value is displayed

























